

Are you a web developer looking for a one-stop solution to test the integrity of your code? Is your website secure enough from being hacked? Our Automated Security Testing Platform (ASTP) is an affordable solution that scans your Java Web Application for vulnerabilities.
ASTP incorporates the three phases of DevSecOps and conducts rigorous testing for every stage of the web development lifecycle. A wide variety of dynamic and static security analysis tools are implemented, including Snyk, SonarQube and Nikto, to ensure a comprehensive scan of your project. With ASTP’s analysis, you can perform debugging and be assured that your final site is secure and ready to be published online.
This application can be enhanced with the following:
Poh Zhi Yuan (Mr.)
Bluetooth technology has become an essential part of our daily lives, enabling us to wirelessly connect and communicate with various devices such as smartphones, laptops, and speakers. However, like all technologies, it is not immune to security vulnerabilities. Without proper security measures in place, Bluetooth can be vulnerable to hacking attempts and unauthorised access.
Goblue is a mobile application that aims to raise awareness about Bluetooth vulnerabilities on users’ device. The app includes features like alerting users of potential threats, scanning nearby devices, and providing tips to improve their device's security. With Goblue, users will be better equipped to protect their device from potential Bluetooth attacks.
This application can be enhanced with the following:
Edmund Wee (Mr.)
Temasek Polytechnic

Have you fallen for fake news before? Fake news is becoming increasingly problematic for online users. The spread of misinformation can manipulate people's perceptions of reality and cause social conflicts. To help users verify the accuracy of online news, we have developed a fake news detector.
Fake News Detector can check whether a site contains fake or real news based on its URL link and/or text content. It uses machine learning, artificial intelligence and natural language processing techniques to analyse the information. This can help to verify the accuracy of news sources and prevent readers from being misled by false information.
This application can be enhanced with the following:
Nurul Arifah Shukor (Ms.)
Temasek Polytechnic

As the frequency and scale of cyber attacks rise, companies are at higher risk of cyber security breaches. Detecting and defending against attacks are becoming increasingly difficult in large-scale networks.
The SDN Defender is a tool to detect and manage cyber attacks in large-scale networks. It makes use of Software Defined Networking (SDN), which leverages software instead of hardware to manage a network. This provides a central control point for network administrators to make changes to the network. By using this centralised control point, SDN Defender enables network administrators to quickly detect and respond to cyber attacks, reducing the risk of data breaches and minimising the impact of the attacks.
This application can be enhanced with the following:
Lim Chee Yang(Mr.)
Temasek Polytechnic
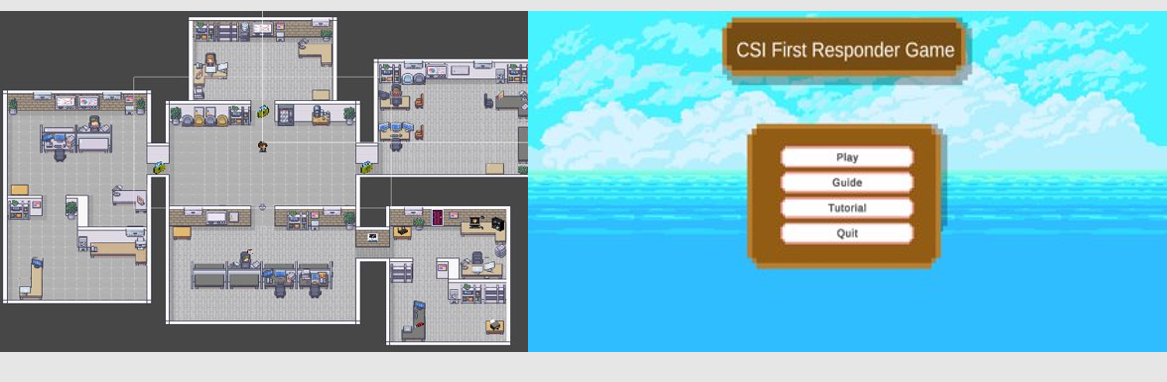
This game is aimed at Year 1 cybersecurity students and people who have a general interest in the field of forensics. This project addresses a common problem in the field of cyber forensics, which is that some individuals may not have the necessary knowledge and training to properly collect as well as analyse digital evidence.
The game is a top-down 2-D role-based player game where the player is a first responder crime scene investigator. Through playing this game, it allows players to learn the technical jargons and core processes of evidence processing to ensure forensics soundness when making the appropriate choices. Players will learn and gain new forensics knowledge as they attempt the game.
This game is educational because it provides resources such as video selections that allow players to learn more about cyber forensics. There is also a well-detailed guide where information based on globally trusted sources can be found so that players can use them in the gameplay. Finally, players can also choose from the five unique scenarios in the game. This allows them to adapt and apply the knowledge accordingly to the different scenarios.
This application can be enhanced with the following:
Seah Chong Poh (Mr.)
Temasek Polytechnic
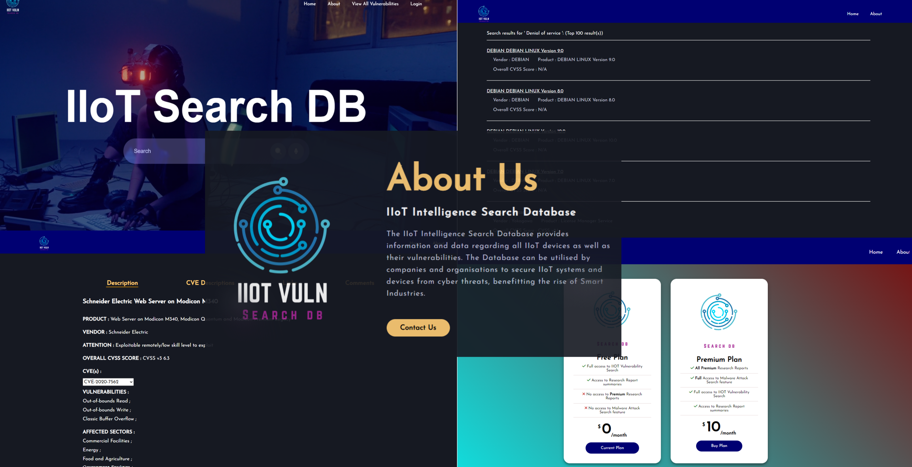
With the rise of Smart Industries devices which allow for more efficient and flexible production capabilities centered around digitalisation as well as Internet of Things (IoT) devices, vulnerabilities are bound to appear. This allows adversaries to exploit the vulnerabilities which can potentially harm organisations and people, either financially or physically. Currently, there is a lack of Industrial IoT (IIoT) focused vulnerability databases that provide vulnerability information regarding IIoT, making it tedious for users to learn about the vulnerabilities pertaining to their IIoT devices.
The IIoT Vulnerability Search Database will serve as a central database that provides vulnerability information regarding IIoT devices. With a central database, users can easily search for IIoT and related Smart Industry device’s vulnerabilities. In addition, the central database also provides information about malware attacks on Smart Industries and IIoT. For example, users would be able to search via the vendor, device name and OS version to see if their IIoT device contains any known vulnerabilities.
This application can be enhanced with the following:
Rosita Jupri (Ms.)
Temasek Polytechnic

MalScape or Malware Escape, is an educational game that boasts a 3D immersive and interactive environment. Learning experience is made exciting for users to attain critical knowledge on Malware through a strong association with puzzle games to keep the learning journey fun and achieve awareness against the malicious threats within the ever-advancing digital world.
MalScape can serve as a secondary option for visitors or allow users with an immersive tour experience as guests within the Malware Analysis Centre that exists only in Temasek Polytechnic. The Malware Analysis Centre at Temasek Polytechnic is the first of its kind in an educational institution in Southeast Asia. It focuses on the detection and identification of malware and forensic investigations. The Centre is unique as it functions as a learning enterprise where students support walk-in clients at the Centre using leading industry technologies and processes.
This application can be enhanced with the following:
Jet Lim.
Temasek Polytechnic
ASTP a.k.a Automated Security Testing Platform is a vulnerability scanning tool that incorporates DevSecOps into the building, testing and releasing phases of your Java Web Application. With the help of Jenkins, GitHub is incorportated for simple linkage of your web application project to ASTP.
Various dynamic and static security analysis tools like, Snyk, SonarQube, Nikto are implemented within the platform to provide a thorough vulnerability scan on your web application. Thus, making your debugging and vulnerability fixing process more efficient and effective.
Mr Poh Zhi Yuan
Covid-19 has resulted employees to work from home, leaving non-tech savvy employees in-charge of the overall security of the remote working laptop. To assist remote working employees, our group has made a program that benchmarks the security portion of the computer and remediate all failed tests. Thus, employees who are not tech savvy can improve and rectify security vulnerabilities found on their computer easily.
Mr. Shaun Tan
Bashvengers is an automated auditing software that scans extensively on various devices. Our tool can conduct automated audit checks on the background with efficiency, solving the tedious and extremely time-consuming process manual auditing is notoriously known for.
Simon (Mr)
The Hacker's Playground is a simulated corporate environment which makes use of virtualization technology and security vulnerabilities to allow students to gain ideas and experience on how cybersecurity skills are applied in real-life, allowing them to demonstrate said skills in the real world.
Sayed Hamzah Alhabshe
Malware Analysis Report is a system and user guide developed with online and offline tools and techniques. It is intended to tackle malware analysis in an efficient and straightforward manner. Hence, simplifying the analysis of sophisticated malware.
Mr. Lim Chee Yong
Today, for every transaction involving numeric data, there is a critical point where data is unencrypted and unprotected, exposing it to be vulnerable against attacks. Our project aims to protect this weakness through empowering a new standard of security that allows for fully encrypted transactions, thereby protecting the data throughout in banks, healthcare, and military.
Chern Nam Yap (Dr)
Current-day auditors are required to run commands one at a time to test the security of a machine. The process is time-consuming, which delays the strengthening of the security of the machine. Through automation, auditors would no longer waste their time running countless audit commands and be quick to jump into risk assessments and then proceed with hardening.
Simon Ngeow (Mr)
The Secure Remote Access project is a webapp that allows users to remotely access equipment at their convenience in a safe manner. This system can be deployed in manufacturing industries, as well as classrooms where hands on sessions could only be conducted in person.
Dr Yap Chern Nam
The problem with Smart Industry Systems are that zero day attacks are on the rise and many organizations need to have a systematic way to identify threats effectively to prevent being targeted by attackers.
Rosita Jupti (Ms.)
Singapore is facing skill shortage in cybersecurity and due to the ever-increasing development of new technologies, there is an increase in the demand of cyber security prospects. Cybersecurity Awareness Challenge is designed to get students to understand what is cybersecurity as well as highlights about the career opportunities in cybersecurity by showcasing tools and techniques used in cybersecurity exploitation, forensics investigation and the numerous possibilities and prospects in the world of cybersecurity.
Our material will be used in the upcoming Youth Cyber Exploration Programme (YCEP) bootcamp conducted by TP in collaboration with Cyber Security Agency Singapore.
Mr. Edmund Wee
SecureAssistant is an app that helps the user to handle basic aspects to keep their computer secure, while cultivating a more cyber secure mindset, packaged in a simple and easy to use GUI. It helps users to block suspicious sites, scan files for malware, secure our passwords and keeps them updated on the latest threats and patches.
It's specific objectives are:
- To perform variety of cybersecurity services.
- To educate
users everyday on recent cybersecurity threats.
- To assist into making your computer more secure
- To protect user's computer
John Leong(Mr)
Software Defined Networking allows the network to be controlled through programming from a centralized location. This project makes use of that to integrate with technologies such as Machine Learning to detect malicious network traffic. By making use of the centralized control point, we can then block the network traffic from one point.
Mr LIM CHEE YONG
Cyber Adventure is a 2D platformer game built using Unity Game Engine. It teaches players of common cybersecurity concepts in a fun and engaging manner.
Jet Lim (Mr)
The virtual machines are created, in the style of capture the flag (CTF), to allow Temasek polytechnic (TP) students from the World Skills Singapore (WSS) to apply and enhance their knowledge and skills of red teaming (or penetration testing). There are different difficulty levels that vary in technical skills which allows the TP students to improve.
Mr Willie Lui
Secure Remote Access Hardening is an automation script written in python. It allows configuration of network switches with user inputs and automatically configures network information of devices previously connected to the switch. Hence, this simplifies the network configuration process and reduces human error and labor costs.
Yap Chern Nam (Dr)
The project leverages the power of Ansible playbooks to revolutionize IT infrastructure management. By automating routine tasks, it optimizes efficiency, minimizes errors and boosts overall infrastructure performance and stability. It's a smarter and more streamlined way to manage your infrastructure.
Lim Chee Yong (Mr)